Phishing again is very hot right now, tax time!
Now assume you are a Small/Medium Enterprise, you have some security controls, it is not perfect (when is it ever) but you have the gear and obviously the online tools as well.
Now enter the problem – we observed a fairly decent phishing attempt today (7th of August 2025), where the malicious actor drafted a well-formatted email. Now, if you are not involved heavily in accounting or tax/business operations, that can look fairly real.
Here is where it gets interesting: the sign-in link is the malicious actor’s landing page, whereas the ATO link is a real link to an ATO page.
Yes, this is more of a end user personalised attack – however – similar login for businesses / sole traders etc etc. Protecting users within your organisation regardless of if its a personal or an organisational targeted attack is still required.
I generally like the personal touch at the top “Please don’t reply to this email.We use hyperlinks to give you more information. If you don’t want to click hyperlinks,you can search for the information on the ATO website.”

We know where the malicious link is, and we have the URL. Let’s look at this from a triage perspective:
- Run the URL through URL Scan
- Run the URL through AnyRun
- Maybe a few others
This is where a junior analyst could run into trouble, because the malicious actor is waiting for that, they have already setup their infrastructure to deal with it.
Example below: AnyRun sandboxing the URL. The malicious actor is front-ending their landing page on Cloudflare and has likely configured web application firewall rules to allow only traffic from an Australian IP address or similar.
Yes, correct, the malicious actors are utilising enterprise security controls, to evade enterprise security controls and checks.
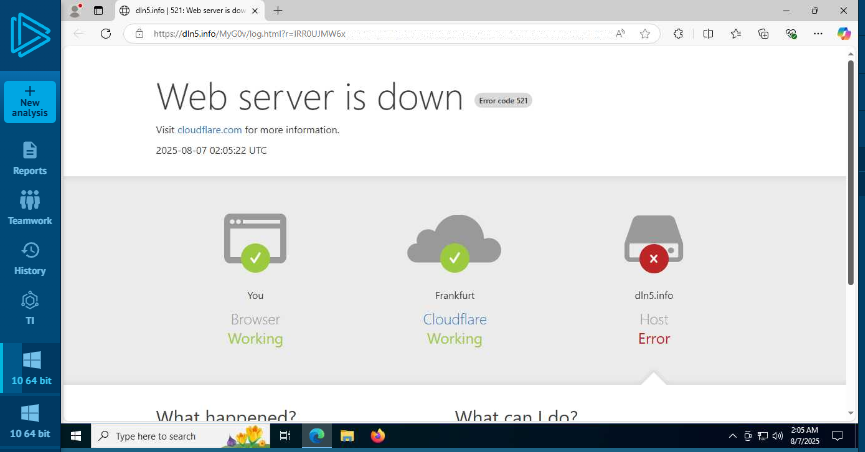
Moving on to another common triage tool – URLScan. Surprise…. same outcome.
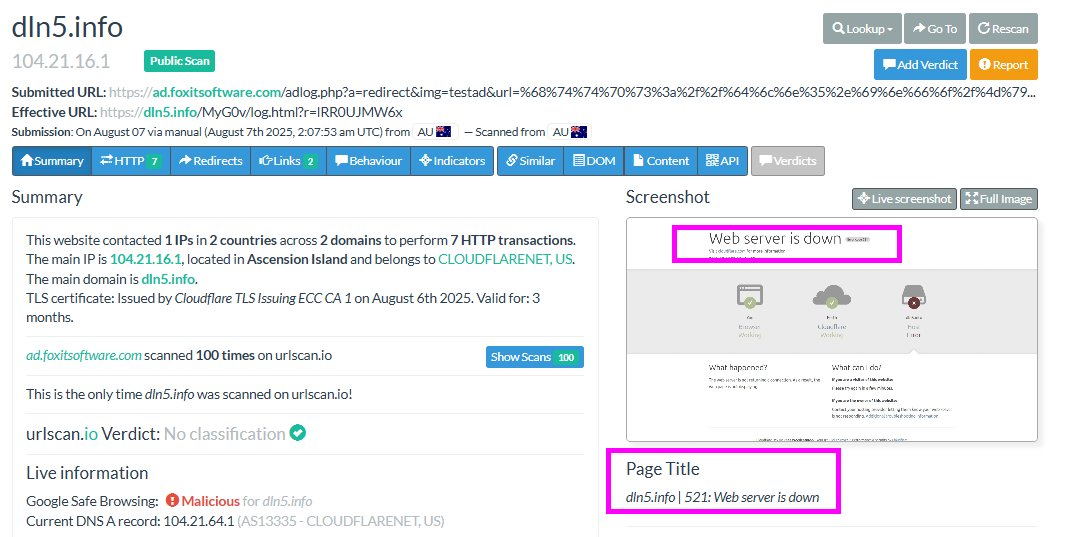
Here is where it gets dangerous: junior analysts could now assume that, since various CERT organisations have detected the issue and a takedown has been put in place, the website is offline, and they should close the ticket.
Sorry, people, the website is actually up. While threat intel sharing is working, Chrome, for example, flags it as malicious, whereas Edge doesn’t care.

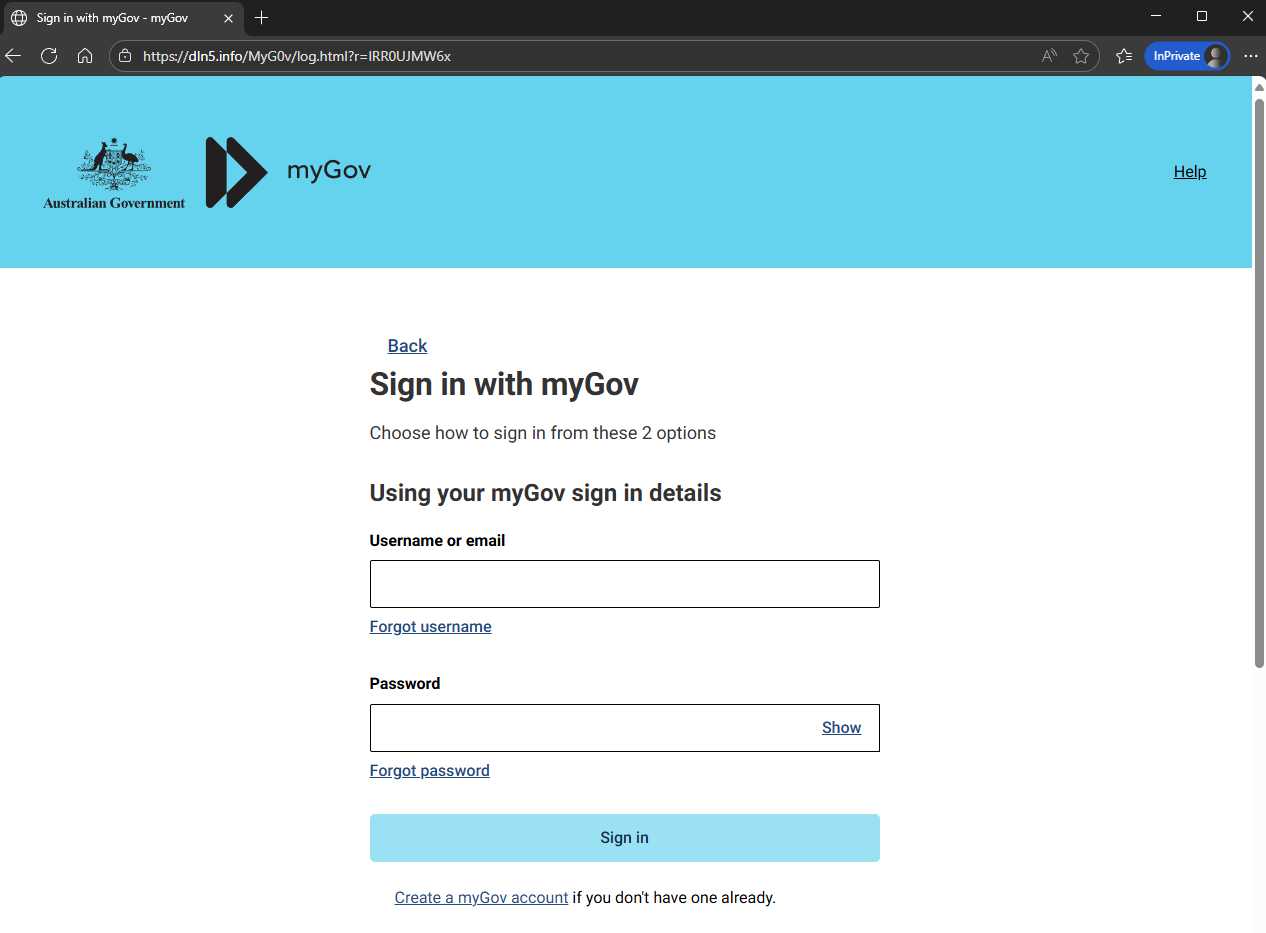
Now consider what will happen:
Junior Analyst
- Ticket was raised
- Analyst had a look
- Appeared fine on the common triage tools
- Ticket closed (already handled upstream)
- Email is still in the mailboxes – still active – still ready to sting users
This is on average 3-5 minutes of triage.
Senior Analyst
This is where experience comes in, a senior engineer/analyst wouldn’t have been satisfied with that, they perhaps would of:
- Had a look at email
- Looked at the source code in the email
- Pulled the malicious link out of the email
- Browsed and interacted with the email to understand intent in a safe manner
- Understood the intent of the attack
- Extracted IOCs
- Blocked / Shared threat intel with relevant teams to block on appropriate security controls
- Push a delete from a security control to remove the email from the email boxes in question
- Close ticket
How long does this take a senior engineer/analyst? About 10 minutes.
The difference? One scenario left the organisation and users at risk, the other utilised experience and maximized the existing investments around them to protect the organisation.
This is not intended on being a beat down on junior analysts by any means, but more to the point – there needs to be access to someone with experience, either internal or outsourced. A 10 minute conversation with a senior analyst will change that junior’s view for the forseeable future – and for the better!
Sometimes the hectic queue clearing tick and flick approach – is the start of your incident.