In the world of infosec, it’s common to see access rules implemented to restrict logins based on the country the user is attempting to log in from and to think of this control as a meaningful one to prevent malicious login attempts from overseas. For a time, this was mostly true, especially as these systems evolved to detect VPNs and proxies that used servers in your home country, but they are no longer.
These days, a threat actor can buy access to proxies that utilise residential ISPs domestically, such as Telstra and Optus, created by infecting someone’s computer with malware. Often, these remote access points used by threat actors are installed by free software, ranging from rewards programs, developer SDKs, and “free” VPN/Proxy software downloaded because the user wants to watch Canadian Netflix.
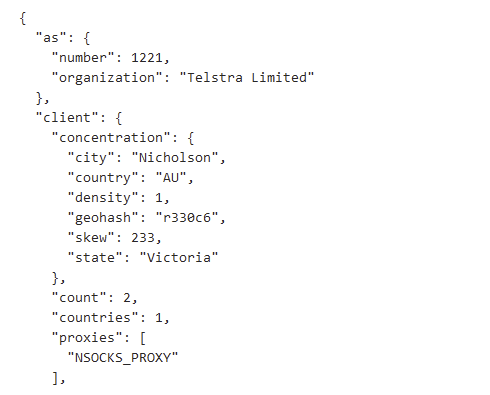
We’ve observed this type of malicious activity take place, completely fool risk-based login protections, and raise no alarms. The login is from the right city, on an ASN and ISP seen before, and MFA was collected from a phishing campaign. How’s your geo-blocking policy stopping that? As an example, we identified these residential IPs linked to NSOCKS proxies, a provider of rental proxies:
There are, fortunately, ways to detect this type of activity. It’s difficult for threat actors to get every aspect of a login correct – the UserAgent or other metadata associated with the login may be slightly off or missing, and of course, for many organisations, company devices are registered, and logins aren’t permitted from unregistered sources.
In addition to this, contextual information about IPs can be correlated with threat intelligence to paint a picture of the history of an IP. Some providers track illegal proxy networks and flag this activity. Integrating an API that can provide this information is another way to add additional layers of scrutiny to each access attempt.
But a threat actor isn’t stopping there. In the past few months, we’ve observed a significant increase in Australian TLDs such as .com.au or .au being used in phishing campaigns, and not as the result of another compromise as you would normally expect.
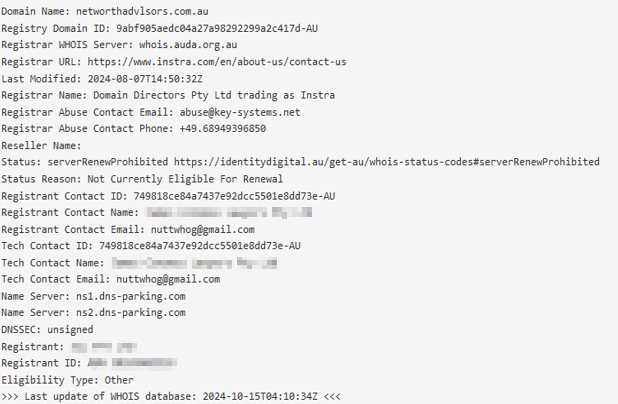
These domains are being purpose-registered to be used in phishing campaigns, bypassing AuDA’s ABN checking by supplying information from a random organisation in the country. How is it that easy? The below domain was used in a phishing attack against Australian businesses, using a Brisbane-based business ABN to register several domains:
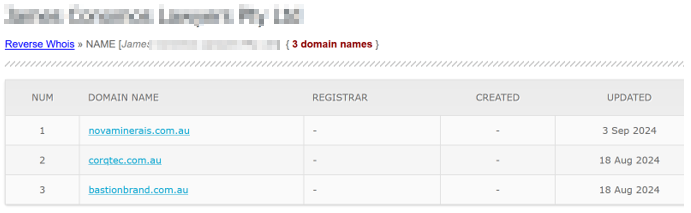
The other domains using the same ABN were also observed in phishing attacks around the same time:
The domains have since been taken down, but they were active for months, plenty of time to cause serious damage. Following up on the Gmail account used to register it, we found examples of domains used for phishing abroad:
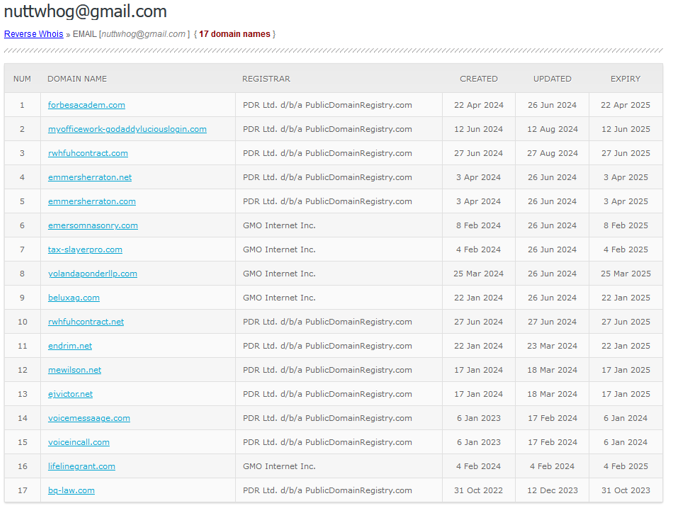
These phishing attacks used domains that were aged enough to bypass basic detection mechanisms and links that passed detection filters from different email protection solutions from the top end of town.
As you can see from the above walkthrough, traditional security controls like Multi-Factor Authentication no longer work, and more preventative security controls like Conditional Access policies are starting to fail at stopping the malicious actors. Robust cyber security practices are no longer just about protection. To be effective, real-time detection and a strong security posture is critical.
We’ve redefined how SOC services function by blending advanced tech with sharp human acumen. We keep 24/7 watch over your digital landscape from our Managed SOC – ensuring any threats are contained and eradicated before they manifest into an avoidable incident.
Reach out to us today for a session to explore your security requirements; when you work with us, you gain both a cyber security solution and a partner. We work to foster relationships based on trust, transparency and mutual respect.
