
In our modern digital landscape, we have an account for everything – with every business we deal with, with every service, and all of them hold some kind of information about us. Each new account increases our risk and before we know it, one of them gets attacked, and our data is now somewhere in the depths of the web being picked apart by scavengers.
On top of this, we have our own risk – from scams, phishing, malicious applications, all of which are pathways that our logins and sensitive information can fall into the hands of threat groups through ‘infostealer’ malware.
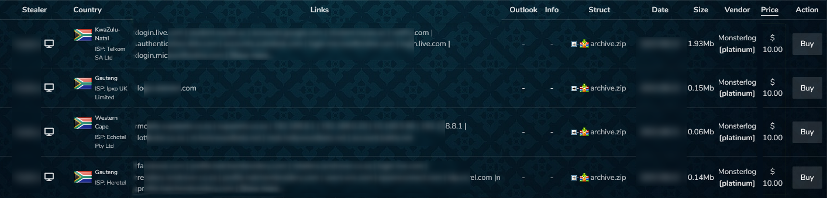
The bad guys typically get their data either from individual malware ‘infostealer’ logs, or from major breaches shared or sold on underground markets. The individual logs are often more valuable in terms of quality, as many markets will sell an individual log ‘pack’ to only one buyer. That buyer may share or leak parts later, but initially, the logins they gain are often valid and ‘fresh’ (as they would call it).
Large scale data breaches from companies can be more valuable in terms of money, but they are noisy i.e. its difficult to sell one without the company being aware, reducing the value of any logins gained, though the personal information of customers such as identity documents and financial information can still be valid despite this awareness.
So how does it get used?
Initial Access
The typical way we’d see stolen data consumed is by criminals using the information to generate initial access into company systems or organisations’ networks, and it works essentially like this:
- Buy ‘fresh’ or source leaked free logs
- Look for company logins used on a personal device (if infostealer), or logins to other companies via B2B users (if from a company breach)
- Test and validate logins to find working ones, establishing a foothold in a company’s network
- Sell the access as an Initial Access Broker (IAB) to another threat actor or group for profit (or use it yourself).

As many of us are guilty of logging into a company system from an unmanaged device i.e. our personal computers, this leaves organisations open to the risk of malicious software being unknowingly installed and company logins stolen. We’ve most often observed this via malicious packages installed by developers, fake ‘cracked’ software, or generic internet scams.
Of course, the above is not an exhaustive list of steps a cybercriminal may take. Some will generate lists of email ‘leads’ to sell or use in phishing campaigns, some will look to use individual logins to conduct their own fraud on a small scale, and some will even use the information to zero in on specific individuals, and conduct targeted financial scams and blackmail.
In the end, what could be the result? Well…
Retail Fraud
In a previous article I spoke about ‘Crabby Store’, a website dedicated to selling cheap access to customer accounts for various services (e.g. Ticketek, Boost Juice, Hoyts Cinemas). Since that article, the site appears to have been sold to a non-Australian entity and users have migrated to other platforms – including the one I’ll speak about below.

Welcome to ‘Bogan Club’. This site operates the same way that Crabby did and has an accompanying Telegram chat for customer support (no, I’m not kidding) and frequent giveaways. The group only has members in the hundreds, and as far as I can tell hasn’t been the subject of any attention online.
Sites like this would typically source valid accounts to sell from bot logs and infostealers – taking advantage of individuals infecting themselves with malware, however the site appeared to sell Total Tools accounts, which we assess is likely sourced from their recent breach.
The group/site operator collaborates with another Telegram user ‘Memezyy’, who has their own group dedicated to selling accounts for food outlets (with no dedicated website, only through private messaging). Based on our OSINT research we assess with high confidence that both individuals are based in Aus, with the Bogan Club operator being based in Melbourne.
Threat actors that operate these websites threaten retail and other B2C organisations by undermining their consumer facing systems and eroding trust between the consumer and the business. Infostealer logs and data breaches give criminals the keys to abuse these systems, where they can leverage tools like OpenBullet and SilverBullet (automated credential stuffing tools) to generate valid logins to sell to their customer base.
How does Tarian leverage this to help organisations?
As we’ve mentioned in previous articles, we use dark net and underground observations to generate cyber intelligence for our customers. Our key differentiator is this is in house built, we are not limited to an asset count, scan cadence or other restrictions commonly observed in this sub domain of cyber.
This intelligence enables us to proactively warn organisations about leaked or stolen information on an ongoing basis, rather than a snapshot / point in time view. We also provide insight on incidents of how they were targeted and where it came from, enabling them to improve their posture to prevent future incidents.
In addition to this, through our attack surface exposure assessments, we use infostealer and breach data to perform reconnaissance and highlight weak points in a company’s environment and show how playing it fast-and-loose with sensitive keys, login information, and corporate infrastructure can lead to compromise without real ‘hacking’ occurring.
